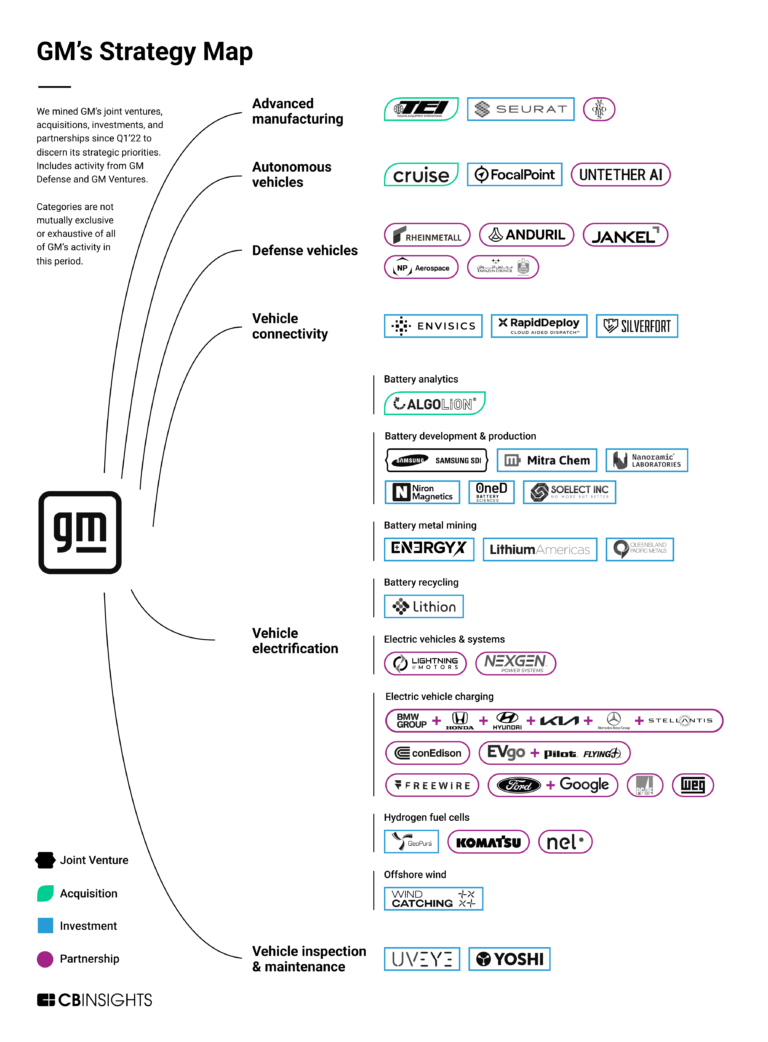
Silverfort
Founded Year
2016Stage
Series D | AliveTotal Raised
$222.6MValuation
$0000Last Raised
$116M | 1 yr agoMosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
+28 points in the past 30 days
About Silverfort
Silverfort focuses on cybersecurity, specifically in the domain of unified identity protection. The company offers a platform that consolidates security controls across corporate networks and cloud environments to prevent identity-based attacks. It uses technology to integrate with existing identity and access management (IAM) solutions, extending its coverage to previously unprotected assets such as legacy applications, information technology (IT) infrastructure, and machine-to-machine access. The platform continuously monitors all user and service account access across both cloud and on-premise environments, analyzes risk in real-time, and enforces adaptive authentication and access policies. It was founded in 2016 and is based in Tel Aviv, Israel.
Loading...
ESPs containing Silverfort
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The multi-factor authentication (MFA) market includes security protocols that require more than one unique credential to verify a user’s identity for a login or other transaction. This provides enhanced security when accessing an organization's data and applications. Many vendors in this market offer adaptive or risk-based MFA solutions, which adjust the required number of authentication steps bas…
Silverfort named as Challenger among 15 other companies, including Microsoft, CyberArk, and Ping Identity.
Loading...
Research containing Silverfort
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned Silverfort in 6 CB Insights research briefs, most recently on Feb 25, 2025.
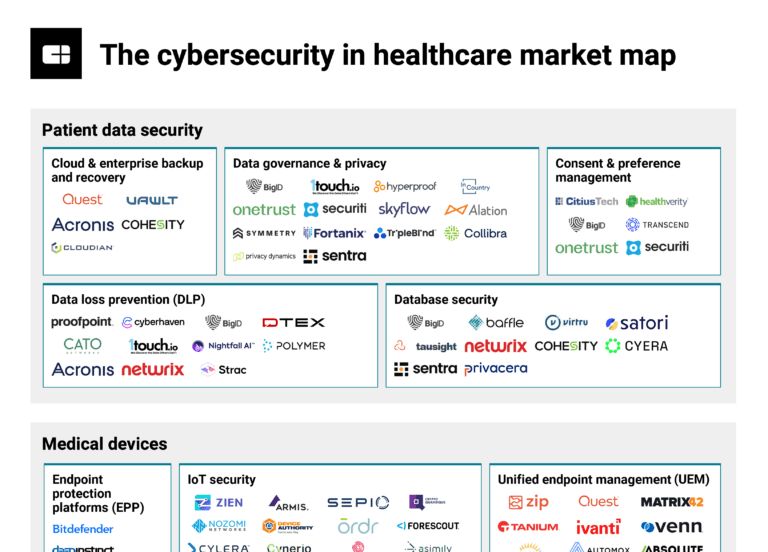
Feb 25, 2025
The cybersecurity in healthcare market map
Mar 14, 2024
The retail banking fraud & compliance market map
Feb 20, 2024
The hardware security market map
Nov 3, 2023
The endpoint security market map
Jul 28, 2023
The cloud security market mapExpert Collections containing Silverfort
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
Silverfort is included in 2 Expert Collections, including Unicorns- Billion Dollar Startups.
Unicorns- Billion Dollar Startups
1,276 items
Cybersecurity
10,957 items
These companies protect organizations from digital threats.
Silverfort Patents
Silverfort has filed 4 patents.
The 3 most popular patent topics include:
- authentication methods
- computer access control protocols
- computer network security

Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
6/19/2018 | 10/17/2023 | Computer network security, Computer security, Intrusion detection systems, Social networking services, Networking hardware | Grant |
Application Date | 6/19/2018 |
|---|---|
Grant Date | 10/17/2023 |
Title | |
Related Topics | Computer network security, Computer security, Intrusion detection systems, Social networking services, Networking hardware |
Status | Grant |
Latest Silverfort News
Jun 23, 2025
Security Boulevard Community Chats Webinars Library Feel Reassured with Advanced Secrets Scanning Technologies Are You Ready for the Future of Cybersecurity? Cybersecurity is not just about human identities anymore. A rising segment of digital focuses on non-human identities (NHIs) – a crucial feature in any contemporary cybersecurity strategy. But what are NHIs, and why should we be paying attention to them? Navigating the Landscape of Non-Human Identities A non-human identity, as the term suggests, is an identity that does not correspond to a human being but a machine entity instead. They are created by combining a unique identifier known as a “Secret” and permissions granted by a destination server. It’s akin to a tourist (the machine identity) using a passport (the Secret) to obtain a visa (the permissions) for their vacation in a foreign country (the system). NHIs are of particular significance – this includes industries like financial services, healthcare, travel, plus departments like DevOps and SOC teams. NHIs help create a secure bridge between security and R&D teams, filling any security gaps that might exist. Effective management of NHIs involves securing both the identities and their access credentials, akin to safeguarding a passport, as well as monitoring their behaviors within the system. Properly handled, this approach can introduce numerous benefits. Unlocking the Benefits of NHI Management A well-implemented NHI methodology can yield various advantages. Here are a few that stand out: 1. Reduced Risk: By actively spotting and neutralizing security risks, NHI management decreases the chances of security breaches and data leaks. 2. Improved Compliance: This approach assists organizations to fulfill regulatory requirements through policy implementation and audit trails. 3. Increased Efficiency: With automated NHIs and secrets management, security teams can concentrate on strategic projects. 4. Enhanced Visibility and Control: Provides a comprehensive view for handling access management and governance. 5. Cost Savings: Lower operational expenses are achieved by automating secrets rotation and NHIs decommissioning. Embracing Advanced Security Technology Advanced security technology emphasizes a comprehensive approach to securing machine identities and secrets by considering all lifecycle stages. This all-encompassing perspective stands in contrast to point solutions like secrets scanning, which offer only limited protection. A variety of NHI management platforms now provide insights into ownership, permissions, usage patterns, and potential vulnerabilities, enabling a much more context-aware security. For example, Forbes Tech Council discusses how emerging technologies are changing cybersecurity. What’s more, these technologies are not a far-off dream, but are already here and being used by businesses worldwide. A report from Research and Markets reveals the rapid shift of organizations to the cloud and the rise of Cloud Security Posture Management. Finding Reassurance in Your Cybersecurity Strategy Ensuring a robust cybersecurity strategy is paramount. Adopting comprehensive NHI management and advanced secrets scanning technology can give organizations the reassurance they need to navigate an increasingly complex digital. While this may seem daunting, the benefits of doing so are clear: reduced risk, improved compliance, increased efficiency, enhanced visibility and control, and cost savings. In other words, a well-executed NHI strategy can provide businesses with a stronger defense against cyber threats, making them more resilient. By leveraging the power of NHIs, your organization can stay ahead of the game, future-proofing your cybersecurity strategy for the challenges and opportunities ahead. So isn’t it time you embraced the future of cybersecurity? Cracking Down the Complexity of Cybersecurity Have you ever thought about how intricate and multifaceted the field of cybersecurity can be? At the heart of this is the concept of non-human identities (NHIs), a burgeoning area in cybersecurity which works to protect machine identities. With more organizations across the globe turn to cloud-based solutions, NHIs transform into an undeniable linchpin in maintaining top-notch security. For example, in healthcare and finance institutions, the secure channel forged by NHIs bridges the gap between R&D and security teams. The result? A more tightly-sealed defense against potential data leaks and security breaches. Organizations cannot afford to ignore the incredible payoff of a well-planned and executed NHI management strategy. Taking Full Advantage of NHI Management When an organization decides to adopt a comprehensive NHI management methodology, they get access to a host of practical benefits, which make all the efforts worthwhile. Here’s a breakdown of the significant advantages: 1. Greater Resiliency Against Attacks: With proactive threat detection and remediation, NHIs reduce the risk of security breaches and data leaks, enhancing the overall system resilience. 2. Better Regulatory Compliance: NHI management simplifies compliance with various laws and regulations by offering policy enforcement and audit trail capabilities. 3. Higher Operational Efficiency: The automation of secret and NHI management lets security teams switch their focus from repetitive tasks to strategic initiatives. 4. Enhanced Oversight: NHI management platforms deliver a holistic view of access governance, enabling more efficient and secure oversight. 5. Cost Effectivity: Automated secrets rotation and decommissioning of NHIs result in significant operational cost savings. Wielding Modern Security Technology Entering a new era of cybersecurity demands an innovative approach. Modern security technology is bringing us a futuristic look at NHIs and their intricate management, transcending the capabilities of traditional secret scanning methods. Robust NHI management platforms take into account not only the ownership and permissions of machine identities, but also their usage patterns and vulnerabilities. This shift towards context-aware security allows organizations to detect threats more accurately and react faster to any potential breaches. Advancements are not distant speculations anymore; they are very much the here and now. With businesses worldwide continue to leverage these technologies, the urgency to incorporate them into your organization’s strategy is more important than ever. Making the Most of the Future Requiring agility and preparedness to counteract unforeseen attacks. NHI management and advanced secrets scanning technologies are paving the way towards resilient cybersecurity strategies that can withstand the challenges of tomorrow. The myriad of benefits that come with a robust NHI strategy equips organizations with a stronger defense mechanism against potential cyber threats. This undoubtedly leads to a more resilient stand against data leaks and security breaches, securing and future-proofing your organization’s pathway. Digital waits for no one, and the time to invest in NHIs is now. Embrace the future of cybersecurity with the power of non-human identities and join the ranks of resilient organizations navigating digital with ease and confidence. For a deeper insight into the complexities and intricacies of NHIs, you can refer to our Silverfort ISA partnership piece and our guide on building an efficient incident response plan . To see how NHIs and security cohesively merge, check out our piece on Entro’s recent partnership with Torq . So, are you ready for the future of cybersecurity?
Silverfort Frequently Asked Questions (FAQ)
When was Silverfort founded?
Silverfort was founded in 2016.
Where is Silverfort's headquarters?
Silverfort's headquarters is located at 30 Ha’arbaa Street, Tel Aviv.
What is Silverfort's latest funding round?
Silverfort's latest funding round is Series D.
How much did Silverfort raise?
Silverfort raised a total of $222.6M.
Who are the investors of Silverfort?
Investors of Silverfort include StageOne Ventures, SingTel Innov8, Citi Ventures, Maor Investments, GM Ventures and 10 more.
Who are Silverfort's competitors?
Competitors of Silverfort include AuthMind and 5 more.
Loading...
Compare Silverfort to Competitors

Sequretek is a cybersecurity company that offers cloud-native cybersecurity solutions. Its offerings include a platform for visibility and threat management, as well as tools for identity protection, endpoint detection and response, and compliance management. The company serves sectors that require cybersecurity measures and regulatory compliance. It was founded in 2013 and is based in Little Rock, Arkansas.

BeyondTrust focuses on identity-centric solutions to manage privileges and access, enabling organizations to oversee their identity attack surface and mitigate threats from both external and internal sources. The company's solutions are aimed at improving identity security and operational efficiencies. BeyondTrust was formerly known as Bomgar. It was founded in 1985 and is based in Johns Creek, Georgia.

AuthMind is an identity security platform that offers solutions within the cybersecurity sector. The company provides a platform for identity security posture management (ISPM) and identity threat detection and response (ITDR), designed to prevent identity-related cyberattacks and secure integrated application landscapes. AuthMind's platform is agentless, easily deployable, and operates across various environments, including cloud, SaaS, and on-premises systems. It was founded in 2020 and is based in Bethesda, Maryland.

BeyondID is a managed identity services provider operating in the technology and cybersecurity sectors. The company offers services such as identity and access management, application modernization, zero trust security, cloud migration, and application integration. BeyondID primarily serves sectors such as healthcare, financial services, and retail. It was founded in 2017 and is based in San Francisco, California.

Transmit Security focuses on providing cloud-native customer identity and access management (CIAM) services. The company offers a range of identity services, including identity orchestration, detection and response, identity management, identity verification, authentication services, and data validation. These services are designed to consolidate identity stacks, centralize decision-making, automate customer journeys, monitor and analyze risk signals, and more. It was founded in 2014 and is based in Boston, Massachusetts.
MightyID is a company specializing in Identity and Access Management (IAM) resilience within the cybersecurity sector. The company offers a suite of tools for backup, restoration, and migration of IAM data, as well as failover and recovery services to ensure business continuity. MightyID primarily serves sectors that require robust identity security and compliance, such as businesses managing large workforces and Customer Identity and Access Management (CIAM). It was founded in 2023 and is based in Irvine, California.
Loading...